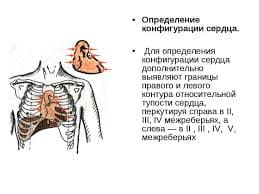
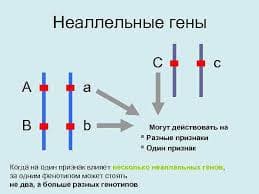
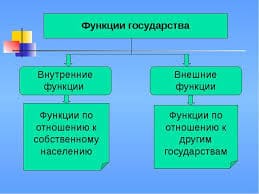
What is eavesdropping?
How can malicious individuals penetrate well-designed, secure computer systems?
What is the difference between denial of service attacks and other exploits?
How can attackers deny service to individual victims?
What are the techniques to exhaust victim’s resources?
What is an indirect attack?
What is a backdoor in a computer system?
What forms may the backdoor take?
 2015-08-21
2015-08-21 271
271