The previous sections introduced gas networks and a concise review of all possible vulnerabilities and risks. This section provides a fairly deep insight into developing plans to evaluate and lower risks in the new economy, and it also tries to help the reader understand key components of risk-management steps.
We defined risk as the possibility of exploitation by an attacker using existing vulnerabilities. "Risk management can therefore be considered the identification assessment, and prioritization of risks followed by coordinated and economical application of resources to minimize, monitor, and control the probability or impact of unfortunate events" [21]. There are many risks associated with the gas industry that are common in other industries, too. Therefore, the need for complete risk- management guidelines is required. A high degree of interconnections between businesses has made identification of the risk of a company a much more difficult task. With the emergence of thermal plants, security of power supply has become highly dependent on the security of the gas supply, which was discussed in depth in the previous section.
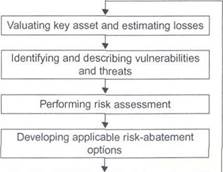
Inspired by the National Petroleum Council [11], a six-step risk-management process that is applicable to the gas industry has been proposed. They are (1) vacating key assets and estimating losses, (2) identifying and describing vulnerabilities and threats, (3) doing risk assessment, (4) developing usable options for risk abatement, (5) analyzing options to select the cost-effective ones, and (5) implementing chosen activities. A schematic view of the steps is depicted in Figure 20.2.
| Figure 20.2 Risk- management steps. |
 Analyzing options to select the cost- effective ones
Analyzing options to select the cost- effective ones
|
| This process should be repeated after a predefined period of time |
I
|
Risk management is a dynamic and continuous process that should be integrated into the culture of organization with an effective policy and promising program to give us what we expect. This dynamic process should be repeated periodically (e.g., annually or every 3 years). It stands to reason that the risk environment,
vulnerabilities, laws, and so on are changing constantly. In the remainder of this chapter we will look carefully at all of the steps.
20.3.1 Valuating Key Asset and Estimating Losses
The first step is to valuate assets and estimate the losses. In this part, the main focus is on determining the value of all assets that exist in the company and whether they are vulnerable. By having the value of each asset, the incurred loss if the asset that was damaged or destroyed can be calculated. Because we want to protect assets that are more vulnerable and would create greater financial losses for a company, a simple rating system that uses qualitative criteria can be used. Furthermore, Vaidya and Kumar [22] reviewed the application of the analytic hierarchy process (AHP) method in order to prioritize and rank different options that can be used as an advanced rating system. According to the National Petroleum Council [11], asset valuation and loss estimation in more sophisticated systems is measured in monetary units. "These values may be based on such parameters as the original cost to create the asset, the cost to obtain a temporary replacement for the asset, the permanent replacement cost for the asset, costs associated with the loss of revenue, an assigned cost for the loss of human life or degradation of environmental resources, costs to public/stakeholder relations, legal and liability costs, and the costs of increased regulatory oversight" [11]. With the appearance of cyber threats and their incredible losses to assets, the estimation of cost has become more difficult. Methods for assessing this value rely heavily on principles of asset management and available data.
Knowing the value of each asset will determine the level of effort that should be made to protect various assets. For example, trade secrets and control systems are vital to all companies, and no insurance company can pay the incurred loss if something bad happens.
For more information on methodologies that can be used to put a value on each asset, readers are referred to asset-management books.
20.3.2 Identifying and Describing Vulnerabilities and Threats
Risk identification tries to find ways in which a company is exposed to risk. This requires an analyst to have at least a primary knowledge of the organization; the legal, social, and political structure of the environment; and the objectives of the organization on an operational and strategic level [23]. In Section 20.2, we discussed many threats and vulnerabilities that exist in gas networks. The problem ere is to identify them. Although every organization can hire outside consultants
perform the job, an in-house worker trained in appropriate techniques (shown in §Ure 20.3) can be used to identify various risks.
Choosing an appropriate technique to identify risk in a company depends on ^апу factors such as the assigned budget. According to Dunjo et al. [24], hazard and °perability (HAZOP) methodology is a process hazard analysis technique used w°rldwide to consider and analyze problems related to hazards and system
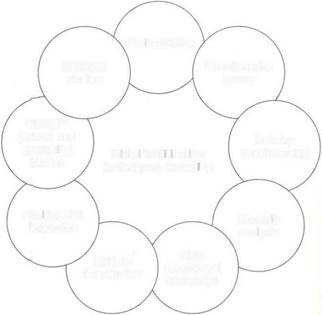
Brainstorming
| Questionnaire survey |
| Business studies |
| HAZOP (hazard and operability) studies |
| Industry benchmarking |
Risk-identification techniques examples
| Auditing and inspection |
| Scenario analysis |
| Risk- assessment workshops |
| Incident investigation |
Figure 20.3 Examples of risk-idcntification techniques [23].
operability by evaluating the impacts of any deviations from design specifications. They present a concise review on all papers published in this area. In business studies, many aspects of a company such as its accountancy, money matters, marketing, and organizational behavior are studied. Questionnaire surveys are methods for acquiring information (usually statistical) about the attributes, attitudes, or actions related to a population with the help of a structurally defined set of questions. Preston [25] provided very good guidelines for the appropriate time to use a questionnaire and efficient ways that can be used to design, construct, administer, and present a questionnaire.
Brainstorming is an individual or group methodology for generating ideas, increasing creative efficiency, and finding solutions to various problems. Accident and incident investigation is a tool for uncovering not only earlier missed hazards but also hazards where loss of controls occurred. "Effective [accident and incident] investigations should be capable of identifying a broad range of factors that may have contributed to an [accident or incident], from an operator's action moments before an [accident or incident] to a senior-level executive decision made years earlier" [26]. As previously noted, vulnerability and threat identification is a dynamic process, especially in the case of cyber risk. After identifying all the risks, we should also describe them in the best formatted manner (may be a standard table is the most useful tool). The first column of each row can be the risk items, and subsequent columns can represent consequence of each risk, its effect on the system, degree of damage that occurred, and class of business activity that was affected
such as tactical, operational, or strategic activities. For example, Lee and Shu [27] used an intuitionalistic fuzzy fault tree analysis (FTA) to Find out the most important components of the system for the problem of failure analysis of a liquefied natural gas (LNG) terminal emergency shutdown (ESD) system to understand weak trail in the ESD and show the areas in which important improvements could be done.
 2015-08-21
2015-08-21 531
531