1. Read and translate the text ”Security risks”.
Spyware:
Spyware is software which is installed without the user’s knowledge and may gather information about that user's internet browsing habits, intercept their personal data, and transmit this information to a third party.
Spyware is often confused with adware. While the two are not the same, there are some similarities.
Some software developers offer their goods as sponsored freeware until you pay to register. If this means you will be viewing sponsored advertisements while the software is being used, it is known as adware.
The adverts usually run in a small section of the software interface or as a pop-up advert box on your desktop. When you stop running the software, or pay to upgrade, the adverts should disappear. Legitimate companies will simply run adverts randomly.
However, some freeware applications which contain adware track user’s surfing habits in order to provide adverts specifically related to the user. When the adware becomes intrusive like this, then it is spyware and it has potential security risks.
Spyware is always considered a malicious program and, is like a Trojan horse, where users unwittingly install the product when they install something else.
A common way to install spyware is to download peer-to-peer file swapping software. Once installed, the spyware monitors user activity on the internet and transmits that information in the background to someone else.
There are often clear signs that spyware has been loaded such as additional browser toolbars or changes to the home page setting. Other signs of spyware infection include pop-up ads which aren't related to the website currently being viewed.
Much like a firewall or anti-virus program, anti-spyware software is crucial to maintain optimal protection and security on your computer and network. Anti-spyware software works by identifying any spyware installed on your system and removing it.
Since spyware is installed like any other application on your system it will leave traces of itself in the system registry and in other places on your computer. Anti-spyware software will look for evidence of these files and delete them if found. This software is now built into a number of antivirus suites.
Phishing and key logging:
Phishing is a form of fraud in which the criminal sends out an email in an attempt to gather personal and financial information from recipients.
The term is adapted from the word fishing, since it involves the same idea that bait is thrown out with the hope that while most will ignore the bait, some will be tempted into biting.
The email the phisher send looks legitimate. Typically, the message will appear to come from a trusted company like Amazon, Paypal or a well-known bank.
It will direct the user to visit the website which looks like the authentic website, where they are asked to update personal information, such as a password, credit card, or bank account details that the legitimate organization already has on record. The website, however, is set up only to steal the information the user enters on the page.
Phishing emails are sent to a large number of recipients. By spamming large groups of people, the scam relies on the email being read by a percentage of people who actually have an account with the legitimate company being taken in by the email and corresponding web page.
Key logging is usually carried out by a form of surveillance software which is able to record every keystroke someone makes to a log file, which is usually encrypted. It can also be carried out by a device attached to the computer keyboard.
A key logger recorder can record instant messages, email, and any information someone types at any time using their keyboard. The log file created can then be sent to a specified recipient. Some key logger programs will also record any email addresses used and website URLs visited.
Key logging software is often used by employers to ensure employees use work computers for business purposes only. Unfortunately, key loggers can also be embedded in spyware allowing your information to be transmitted to an unknown third party.
Unlike other types of malicious program, key loggers present no threat to the system itself. However, they can pose a serious threat to users, as they can be used to intercept passwords and other confidential information entered via the keyboard.
As a result, cyber criminals can get PIN codes and account numbers for e-payment systems, passwords to online gaming accounts, email addresses, user names, email passwords etc.
Key loggers can be used as tools in both industrial and political espionage, accessing data which may include proprietary commercial information and classified government material which could compromise the security of commercial and state-owned organizations (for example, by stealing private encryption keys).
Online fraud and identity theft:
Fraud is described as wrongful or criminal deception intended to result in financial or personal gain. Online fraud can be defined as the use of internet services or software with internet access to defraud victims or to otherwise take advantage of them.
In other words it is traditional fraud, but with the internet as the means of carrying out the fraud.
Like its traditional counterpart, online fraud can take many forms. Action Fraud, which is the UK’s national reporting centre for fraud and internet crime lists a total of 30 recognized types of online fraud.
These include: account takeover, advance fee frauds, bank card and cheque fraud, charity donation fraud, domain name scams, holiday fraud, internet auction fraud, mass marketing scams etc. Phishing is a form of online fraud.
Identity theft is a very specific form of online fraud. Identity theft is the crime of obtaining the personal or financial information of another person for the sole purpose of assuming that person's name or identity in order to make transactions or purchases.
Phishing emails are a common means of acquiring the details to carry out the identity theft.
Individuals can protect themselves from online fraud or identity theft by:
· Not giving any personal information to anyone before verifying their credentials.
· Not responding to emails asking them to click on a link and confirm bank details. Banks do not update data in this way.
· Destroying and preferably shredding receipts with your card details on or mail containing name and address.
· Making sure their computer has up-to-date anti-virus software and a firewall installed.
· Ensuring their browser is set to the highest level of security notification.
Denial of service (DoS) attacks:
A DoS attack is an explicit attempt by attackers to prevent legitimate users of a network resource from using that service. The classic DoS attack will come from a single computer sending multiple requests to that resource.
There are two general forms of DoS attacks:
· attacks with crash services
· attacks with flood services
Many DoS attacks exploit limitations in the TCP/IP protocols. For all known DoS attacks, there are software fixes that system administrators can install to limit the damage caused by the attacks. But, like viruses, new DoS attacks are constantly being dreamed up by hackers.
Distributed denial of service attacks (DDoS):
It has become common practice for extortionists to target internet firms and threaten to cripple their websites with deluges of data unless they pay a ransom. These are known as distributed denial of service (DDoS) attacks and they overwhelm servers with requests until they are forced offline.
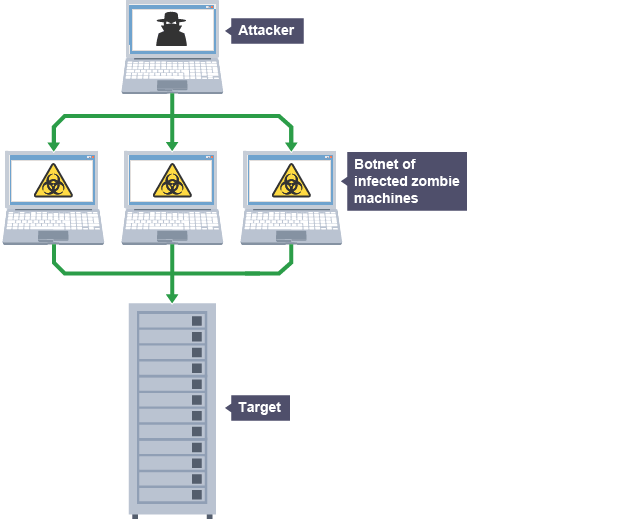
Computers from all over the world are innocently recruited to take part in the attack, each sending only a small part of the entire data flood. The recruiting of machines to take part in attacks is typically done by infecting them with a virus, Trojan horse or worm.
The IP address of compromised machines - called zombies or bots - is sent back to the criminal, who will use it to launch a DDoS. The network of zombie machines is sometimes known as a Botnet.
2. Answer the questions.
1) What software is called malicious?
2) What does spyware do?
3) What is phishing?
4) What are software products from reputable companies, where you will be viewing sponsored advertisements until a commercial fee is paid, known as?
5) Which malicious activity is equally as dangerous for large corporations as it is for the individual user?
6) What is identity theft?
7) What should you do to prevent online fraud?
8) What is the name given to a computer on the Internet which has been compromised by a hacker with a view to be used in a DDoS?
9) What name is given to the group of compromised computers which are used in a DDoS?
10) Which actions are carried out on a compromised computer in a DDoS attack?
3. Summarize the content of the paper.
4. Speak about the problem of security in computer technologies.
 2015-10-14
2015-10-14 1915
1915