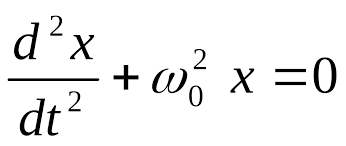Read the following article to find out:
1. What computer hacking is?
2. Why the hackers do what they do?
3. How seriously companies are taking the problem?
You can rob the bank without leaving the house these days. Who needs stocking masks, guns and getaway cars? If you’re a computer whizz-kid, you could grab your first million armed with nothing more dangerous than a personal computer (PC), a telephone and a modem to connect them.
All you have to do is dial into the networks that link the computers in large organizations together, type in a couple of passwords and you can rummage about in the information that stored there to your heart's content.
Fortunately it isn't quite as easy as it sounds. But, as more and more information is processed and stored on computer, whether it's details of your bank account or the number of tins of baked beans in the stockroom at the supermarket, computer crime seems set to grow.
A couple of months ago a newspaper reported that five British banks were being held to ransom by a gang of hackers who had managed to break into their computer. The hackers were demanding money in return for revealing exactly how they did it. In case like this, banks can consider paying just so they can protect themselves better in the future.
No one knows exactly how much money is stolen by keyboard criminals - banks and other companies tend to be very secretive if it happens to them. It doesn't exactly fill customers with confidence if they think their bank account can be accessed by anyone with a PC! Some experts believe that only around a tenth of all computer crimes are actually reported. Insurance company Hogg Robinson estimate that computer frauds cost British companies an incredible £ 400 million a year.
Most computer crimes are “inside jobs ”, where staff with access to the company's computers fiddle with the records. A comparatively small amount are committed by the more glamorous- and headline- grabbing- hackers.
The true hacker, it seems, doesn't do it for financial gain. The thrill appears to be not in getting rich, but in beating the system. Two of Britain's most notorious hackers are Nicholas “Mad Hacker ” Whiteley and Edward Singh. The renegade pair has been the scourge of organizations with insecure computers for years, seemingly competing for the title of Britain’s best hacker.
Whiteley’s hacking days came to an abrupt halt in June, When the 21-year-old was sent to prison for four months for damaging computer disks. Edward Singh first came to public attention after claiming that he had hacked into American and British government and military computers.
‘’ It has never been my intention to steal anything, ‘’ said Singh. ‘’ I really see myself as a highly skilled software engineer. ‘’ His mission seems to be to prove just how insecure their systems are.
AS with everything else, hackers start young in the States. A 12- year-old boy in Detroit was accused of entering a company’s credit rating computer and distributing the numbers he found there. His mother told reporters that he spent up to 14 hours on his computer during the weekend. ‘’He didn’t bother me ‘’ she said. ‘’ I figured computers, that’s the thing of the day.’’
Last month two New-York teenagers, one aged 14 and one aged 17, were charged with breaking into a computer system owned by a company that publishes computer magazines. They are alleged to have changed polite recorded greetings to rude massages, added bomb threats and wiped advertisers orders.
Customers linked into the system only to be told that ‘’ Daffy Duck is not available ‘’! The company estimates that the tampering has cost $2.4 million.
Prevention is probably easier than detection, and many companies now spend lots of time and money devising programs using passwords and codes. Of course, all this is no use at all if computer users tell each other their passwords, stick it on the screen so the don’t forget it or use passwords like ‘’ password ’’. It all happens.
There are plenty of software companies who specialize in writing software that make computers hacker-proof. One company in the States set out to prove that its system can defeat hackers by asking over 2 000 of them to try to hack in. The Hackers were given two weeks to discover the secret massage stored on two PCs in o9ffices in New –York and San Francisco. The massage reads: ‘’The persistent hunter who wins his prize sooner or later becomes the hunted.’’ You’ll be relieved – or perhaps disappointed –to learn that not one hacker managed it.
Find words or phrases in the text that means the same as:
a. expert (especially at a young ag) _____________________
b. search through _____________________
c. as much as you want _____________________
d. be called up on a computer screen _____________________
e. make small changes / interfere with _____________________
f. rebellious / lawless _____________________
g. caused a lot of trouble to _____________________
h. aim in life _____________________
i. removed completely _____________________
j. interfering with (without permission) _____________________
Now complete these statements by choosing the answer, which you think, fits best.
1. Banks may pay computer criminals
a. to give back information they have stolen.
b. to explain what their technique is.
c. not to commit the same crime again.
d. not to pass on information they have stolen.
2. Companies don’t always report computer crime because they
a. think it would create bad publicity.
b. don’t expect the criminals to be caught.
c. don’t want the police to investigate.
d. think the criminals are members of their staff.
3. The computer hackers’ motive seems to be
a. to win a competition.
b. to make a lot of money.
c. to overcome a challenge.
d. to appear in the newspapers.
4. The mother of the 12- year- old hacker in Detroit
a. had been worried about the time her son spent at his computer.
b. thought her son’s interest in his computer was normal.
c. had been involved in her son’s criminal activity.
d. had tried to prevent her son’s criminal activity,
5. What was the result of one software company’s attempt to prove that its security systems were effective?
a. It was a complete success.
b. It was a partial success.
c. It was a failure.
d. the results were inconclusive.
Text – 2
Teens in Cyberspace
1 Read the passage and fill in the mini- cloze (one or more words in each blank) to summarize the main idea.
I
Knowing where to draw the line isn’t easy; admit moms and dads regarding the question of supervision of their teenage children as they roam around cyberspace. Yet, many families are wrestling with the issue, as the number of home computers and teenagers with online access grows daily.
II
Many teens believe that those who don’t know the online world misinterpret it as dark and dangerous. ‘’ I think parents worry because it’s something they couldn’t do when they were kids,’’ says Kristel Sharman, 13, of Georgetown, Delaware. ‘’ Most people don’t understand what the Net is all about, that’s why they’re freaking about over it, ‘’ adds Wayne, 15, of Winnipeg. To Wayne and his friends, cyberspace is more like a utopian refuge. ‘’ Before I was online, I must say I was m a lost child, ‘’he says. ‘’ I’ve grown so much because I was able to talk openly to people. No one on line thinks about your age or eye color or skin color or anything. They see you from the inside. ‘’
III
‘’ It’s like an alternative world in some ways, ‘’ says Lindsay Andrews, 17, from Georgia. ‘’ It’s the same as having a big group of friends, but you don’t see what anyone looks like. It’s like the ideal that everyone speaks of when they say you should judge people based on race, age, sex, etc.’
IV
Traditionally, the teen years are ‘’a time to try new things, experiment with identity and ideas, have passionate friendships,’’ says psychologist Sherry Turkle of MIT, who studies kids and online world. ‘’If you had to imagine a medium that was tailor- made for addressing some of those needs and demands, you almost couldn’t do better than the online world.‘’ To teens, the Net ‘’ represents independence and freedom, ‘’ says Eileen Shiff, editor of the book Experts Advise Parents. ’’ There aren’t any boundaries, and the world opens up to them. ‘’
V
For parents, safety is a primary concern. ‘’ I think a lot of parents have a great need to over- control their teenagers out of fear and wanting to keep them safe, ‘’ says Kathy McCoy, author of the teen guide Life Happens. She adds that while teens do need some ground rules, it’s important for parents to give them some space to roam free a bit without trying to control every aspect of their lives. ‘’ They want very much to expand their worlds, and being online really allows them to do a lot of experimenting in a low- risk way without leaving home.’’
VI
‘’ For parents who haven’t been initiated into the cyber-age, it may feel more threatening than it needs to be. Parents should know what it is to surf the Net, what chat groups are, what’s on some of the sites their children visit. In some ways, this may calm their fears because at least they’ll know what they’re dealing with. There need to be rules about online use, just as there are rules about using the family car, talking on the phone or anything else. But as with many teenage activities, parents can’t be there to monitor 24 hours a day’’.
I - Many ………………………………… don’ t really know how ………
…………….. Internet use.
II - ………………feel that parents don’t really …………………… the
online world.
III – In the online world, …………………………….. is judged by what
he looks like.
VI – One expert says that …………………….. is a perfect place for
teenagers to ……………………….
V - ………………………… should not try to over- control …………….
VI – However, there must be some clear……………………….. for
Internet use in the same way that there are rules for ………..
2 Discuss in groups:
- the advantages and disadvantages of using Internet by teenagers.
Text-3
THE IDEA MAN
What computer and software companies do you know?
Which company did each of these people create?
 2017-11-01
2017-11-01 2158
2158