Explain the Hash function by using the general formula. Give an example of hash algorithm.
can be applied to any sized message M
produces fixed-length output h
is easy to compute h=H(M) for any message M
given h is infeasible to find x s.t. H(x)=h
one-way property
given x is infeasible to find y s.t. H(y)=H(x)
weak collision resistance
is infeasible to find any x,y s.t. H(y)=H(x)
strong collision resistance
ex:Bithday algorithm
Describe the Direct Digital Signature.
involve only sender & receiver
assumed receiver has sender’s public-key
digital signature made by sender signing entire message or hash with private-key
can encrypt using receivers public-key
important that sign first then encrypt message & signature
security depends on sender’s private-key
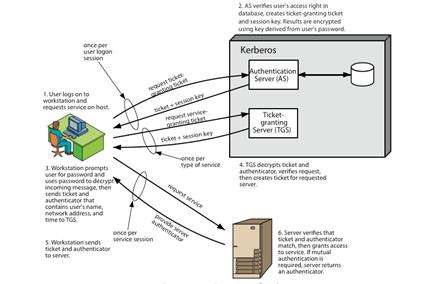
Kerberos: Give description, short dialogue between user and server.
trusted key server system from MIT
provides centralised private-key third-party authentication in a distributed network
allows users access to services distributed through network
without needing to trust all workstations
rather all trust a central authentication server
two versions in use: 4 & 5
- obtain ticket granting ticket from AS
• once per session
- obtain service granting ticket from TGT
• for each distinct service required
- client/server exchange to obtain service
• on every service request
 2015-08-21
2015-08-21 288
288








