Ø three broad lines of defense:
1. attack prevention & preemption (before)
2. attack detection & filtering (during)
3. attack source traceback & ident (after)
Ø huge range of attack possibilities
hence evolving countermeasures
Information Security
Final
2-variant
Name, surname: Group:
Good Luck!!!
Questions: (1-10 questions are main and q.11 is bonus)
1) Write down AES operations in right order for one round:
2) Write down the Diffie-Hellman Key exchange alg. step by step in right order without an example and for two sides.
3) Explain the MAC by using the general formula. Give an example of MAC algorithm.
4) Describe the Arbitrated Digital Signature.
5) X.509: Give description and definitions of the following: Certificate, and CA?
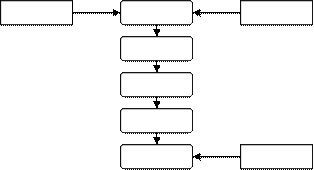
6) What is the algorithm of message receiving in PGP? Number below operations in the right order.
… PGP retrieves the sender's public key from the public-key ring, using the Key ID field in the signature key component of the message as an index.
… PGP recovers the transmitted message digest.
… PGP then recovers the session key and decrypts the message.
… PGP computes the message digest for the received message and compares it to the transmitted message digest to authenticate.
… PGP prompts the user for the passphrase to recover the unencrypted private key.
… PGP retrieves the receiver's private key from the private-key ring, using the Key ID field in the session key component of the message as an index.
7) What are the types of ‘modes’ that involve in IPSec? Describe these modes in few words.
8) Describe SSL Record Protocol involving in SSL.
9) Describe the Intrusion Detection System. What is a Rule-based detection?
10) What is a Firewall? Name configurations of Firewall and describe any one of them.
11) What is Malicious Software? Describe Worms and their phases.
 2015-08-21
2015-08-21 330
330