Trojan Horse
31. Decipher the message IAIWWT using the Hill cipher with the inverse key 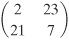 .
. 
ONALLY
32.Decipher the message YITJPG using the Hill cipher with the inverse key
Take the indices of letters according to the given table.
DIFFIC
33.A form of cryptosystem in which encryption and decryption are performed using the same key. Also known as conventional encryption.
Symmetric encryption
34.______________ is the science and art of transforming messages to make them secure and immune to attacks.
Cryptography
35.Decipher the ciphertext QMHXIVQ using Caesar Cipher with the key=4.
MIDTERM
36.Encrypt the message "HELLO" using the Hill cipher with the key 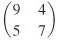
 Take the indices of letters according to the given table.
Take the indices of letters according to the given table.
BLNCKX
38.Encrypt the message WELCOME! using Caesar Cipher with the key = 5.
BJQHTRJ!
39.Encrypt the message WELCOME! using Caesar Cipher with the key = 34
EMTKWUM!
40.Embedded in a computer program that checks for a certain set of conditions to be present on the system. When these conditions are met, it executes some function resulting in unauthorized actions.
Logic Bomb
41.Find d using the RSA algorithm, if p = 3; q = 11, e = 7; M = 5.
42.Find d using the RSA algorithm, if p = 5; q = 11, e = 3; M = 9.
43.Free from mistake or error and having the value that the end-user expects.
Accuracy
44.How does the Social Engineering work?
People write passwords in different places and disclose passwords naively to others
45.How does the Dictionary attack work?
Hacker tries all words in dictionary to crack password
46.How does the Dumpster Diving work?
People dump their trash papers in garbage which may contain information to crack passwords
47.How does the Brute Force attack work?
Try all permutations of the letters and symbols in the alphabet
48.How can we protect the system?
Setup IDS
Encrypt important data
Setup firewall
49.If a key is 8 bits long, how many possible numbers that the key can generate?
Ответ: 256
50If a wrong key is entered to decrypt a message, what will happen?
The output will be gibberish
51.If the encrypted message is XBPG and deciphered text is QUIZ using Caesar Cipher, what is the value of key?

52.DMZ What is one advantage of setting up a DMZ with two firewalls?
You can control where traffic goes in the three networks
53.In an RSA system, the public key of a given user is e = 31, n = 3599. What is the value of p and q?
p = 61, q = 59
54.In an RSA system, the public key of a given user is e = 31, n = 3599. What is the φ(n)?
φ(n) = 3480
55.In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the value of p and q?
p=5, q=7
56.In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the plaintext M?
57.In a public-key system using RSA, you intercept the plaintext M = 13 sent to a user whose public key is e = 5, n = 35. What will be the ciphertext C?
58.In a public-key system using RSA, you intercept the plaintext M = 25 sent to a user whose public key is e = 5, n = 35. What will be the ciphertext C?
59.In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the value of p and q?
q=7, p = 5
60.In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the φ  ?
?
61.In a public-key system using RSA, you intercept the ciphertext C = 10 sent to a user whose public key is e = 5, n = 35. What is the value of d?
62.Malicious attempts by a single person or a group of people to cause the victim, site, or node to deny service to its customers
Denial of Service Attack
63.Match each term according to their meanings in Public-Key Cryptosystem
| Ciphertext: this is the scrambled message produced as output | ||
| Encryption algorithm: the algorithm performs various transformations on the plaintext | ||
| Decryption algorithm: this algorithms accepts the ciphertext and the matching key and produces the original plaintext | ||
| Plaintext: this is the readable message or data that is fed into algorithm as the input | ||
| Public and private keys: this is the pair of keys |
64.Weaknesses of a system that could be accidentally or intentionally exploited to damage assets.
Vulnerability
65.One objective of cryptography is keeping information secret from all but those who are authorised to see it. The term referring to this is:
Confidentiality
66.One objective of cryptography is property of being accessible and useable upon demand by an authorized entity.
Availability
67.One objective of cryptography is conveyance, to another entity, of official sanction to do or be something. The term referring to this is:
Authorisation
68One objective of cryptography is ensuring information has not been altered by unauthorised or unknown means. The term referring to this is:
Data integrity
69.One objective of cryptography is identifying and acknowledging the identity of entity. The term referring to this is:
Identification
70.One objective of cryptography is prevention of authorized access to resources or the delaying of time-critical operations.
Denial of service
71.One of the two keys used in an asymmetric encryption system. For secure communication, the ___________ should only be known to its creator.
private key
72.One of the two keys used in an asymmetric encryption system. The ____key is made ________, to be used in conjunction with a corresponding ______________key
Public, public, private
73.One of the most famous documented DDoS attacks Back. How does the Back work?
Attack is launched against an apache Web server, which is flooded with requests containing a large number of front-slash (/) characters in the URL.
74.One of the most famous documented DDoS attacks Mailbomb. How does the Mailbomb work?
The victim's mail queue is flooded by an abundance of messages, causing system failure.
75.One of the most famous documented DDoS attacks Land. How does the Land work?
The attacker sends the victim a TCP SYN packet that contains the same IP address as the source and destination addresses. Such a packet completely locks the victim's system
76.One of the most famous documented DDoS attacks CrashIIS. How does the CrashIIS work?
The attacker sends the victim a malformed GET request, which can crash the Web server
76.One of the most famous documented DDoS attacks Apache2. How does the Apache2work?
The client asks for a service by sending a request with many HTTP headers resulting Apache Web server to crash
77.Perform encryption using the RSA algorithm, if p = 3; q = 11, e = 7; M = 5.
78.Perform decryption using the RSA algorithm, if p = 5; q = 11, e = 3; C = 14.
79.Provides a user with protection against discovery and misuse of his or her identity by other users.
Privacy
80.Program that can replicate itself and send copies from computer to computer across network connections. Usually performs some unwanted function.
Worm
81.Program that consumes system resources by replicating itself.
Bacteria
82.Possibility of an incident or attack to cause damage to your enterprise
Risk
83.Set of hacker tools used after attacker has broken into a computer system and gained root-level access.
Rootkits
84.Secret undocumented entry point into a program, used to grant access without normal methods of access authentication.
Trapdoor
85.The translation of encrypted text or data (called ciphertext) into original text or data (called plaintext). Also called deciphering.
Decryption
86.The key used in a symmetric encryption system. Both participants must share the same key, and this key must remain secret to protect the communication.
Secret key
87.The quality or state of being genuine or original, rather than a reproduction or fabrication.
Authenticity
88.The quality or state of having ownership or control of some object or item.
Possession
89.The process of verifying and identity claimed by or for a system entity.
Authentication
90.The Vigenere cipher is which of the following types:
Polyaplhabetic
91.The Caesar cipher is a __________ cipher that has a key of 3.
Shift
92.The best-known multiple-letter encryption cipher, which treats digrams in the plaintext as single units and translates these units into ciphertext digrams
Playfair cipher
93.The word "asymmetric" in public-key cryptography means:
The key to encrypt is different from the key to decrypt
94.The_______________ is a widely used cryptographic hash function that produces a 128 –bit (16byte) hash value
MD5 Message Digest alghorithm
95.The _______________ is a number or a set of numbers on which the cipher operates.
Key
96.Use the Playfair cipher with the keyword "PLAYFAIR" to decrypt the message "YPYQ".
AFAS
96.Use the Playfair cipher with the keyword "PLAYFAIR" to encrypt the message "GOTO".
OVNQ
97.Using this Playfair matrix decipher the message: UZTB
MUST
98.A process of identifying, analyzing and controlling critical information.
OPSEC
99.Which of the following statements is the definition of IP Spoofing - Source Routing?
Attacker spoofs the IP address of another machine and inserts itself between the attacked machine and the spoofed machine to intercept replies.
100.Using this Playfair matrix encrypt the message: Cadogans
TG TU ER VF
101.Using Magic square cipher decipher the message “..S….NS…IE…O.S..” with the key 5 and generated magic square
SEESSION
102.Using Magic square cipher encrypt the message “MAJOR” with the given key 3
.M..RJA.O
104.Using Feistel Cipher some information was encrypted, as the ciphertext scrambled message with the length 4n bits was outputted. What is the bit length of initial plaintext?
4n
105.Weakness of a system that could be accidentally or intentionally exploited to damage assets
Vulnerabilities
106.What is Encryption algorithm?
Performs various substitutions and transformations on the plaintext
107.What is Data integrity?
Ensuring information has not be altered
108.What is Decryption algorithm?
takes the ciphertext and the secret key and produces the original plaintext
109.What is Hacking?
Hacking refers to an array of activities which are done to intrude some one else's personal information space so as to use for malicious, unwanted purposes
110.What is Cracking?
All of the statements
111.What is Phreaking?
Phreaking is basically hacking with a telephone. Using different "boxes" and "tricks" to manipulate the phone companies and their phones, you gain many things.
112.What is plaintext?
The original intelligible message or data that is fed into the algorithm as input
113.What does a firewall do?
Protects your computer from Internet intrusion
114.What should do after hacked?
All of the statements
115.What will be the value of key in Caser Cipher if initially key=65?
116.Which attack takes advantage of the way in which information is stored by computer programs?
Buffer overflow attacks
117.Which one of the statement is a formula to find cipher in RSA?
c = me (mod n).
118.Which one of the statement is a formula to find plain in RSA?
m = cd (mod n)
119.Which of the following statements is the definition of Session Hijackig?
Process of taking over an existing active session
120.Which of the following statements is the definition of E-mail Spoofing?
Attacker sends messages masquerading as someone else
121.Which of the following statements are types of Spoofing?
IP Spoofing
Web Spoofing
Email Spoofing
122.Which of the following statements are types of Firewalls?
Application-level gateways
Packet filtering
Circuit-level gateways
123.Which of the following statements is the definition of IP Spoofing - Flying-Blind Attack?
Attacker uses IP address of another computer to acquire information or gain access.
124.Which of the following statement(s) is(are) the Security Principles?
All of the statements
125.Which of the following statement(s) is(are) ingredients for a public-key encryption scheme?
All of the statements
126.If you encrypt a ciphertext using right key, you will get:
 2015-08-21
2015-08-21 695
695